It’s not just another IT-project.
It’s about being ready.
NIS2 is the driver for your OT Security!
The essentials of NIS2
What?
Binding Requirements for Cyber and OT Security
The EU’s NIS2 Directive establishes a clear legal framework. It mandates reporting obligations, minimum security standards, and specific requirements for companies with critical operations.
Why?
A New Threat Landscape Demands Equal Protection for IT and OT
Cyberattacks no longer target just IT; they increasingly affect operational technology. NIS2 requires comprehensive protective measures for all networked systems.
Who?
160,000 Companies Across Numerous Sectors Are Affected
The updated definitions of critical infrastructure now include many medium-sized businesses. Energy, transport, health, manufacturing, and other sectors are all obligated to comply.
When?
The Benefits of Early Preparation
Organizations that review and adapt their security measures to meet NIS2 standards now will not only ensure timely compliance, but also significantly boost their operational resilience.
A Closer Look at OT Security
Operational Technology (OT) controls and manages physical processes in industry, building management, transportation, and critical infrastructure. Unlike Information Technology (IT), which handles data, OT is responsible for production processes and the control of machinery and equipment.
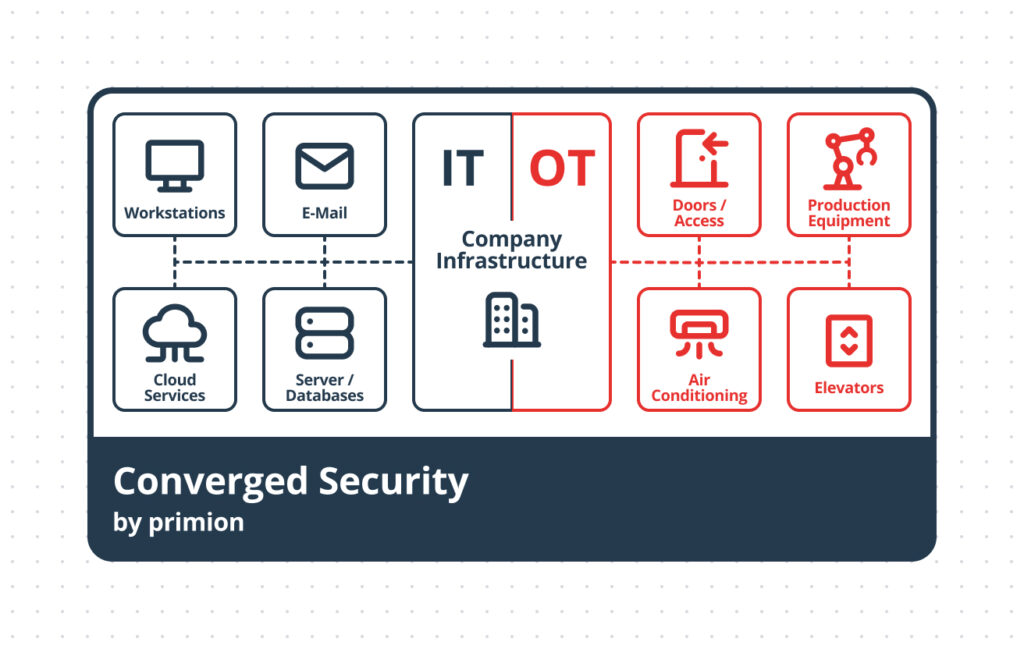
Examples of Common OT Systems
Building Automation
- HVAC systems, lighting, fire protection systems, electronic access control, and elevators are standard in most office buildings.
Industrial Control Systems
- Automotive: Robotic controls in manufacturing lines.
- Pharmaceuticals: Dosing and process control systems.
- Manufacturing: CNC machines, presses, and conveyor systems.
- Logistics & Warehousing: Conveyor belts and sorting systems.

Primion is certified according to the world’s leading standard for cybersecurity in the scope of hardware and software development of access control, time and attendance, production data recording systems and hazard management systems.
Why It’s Crucial to Act Now
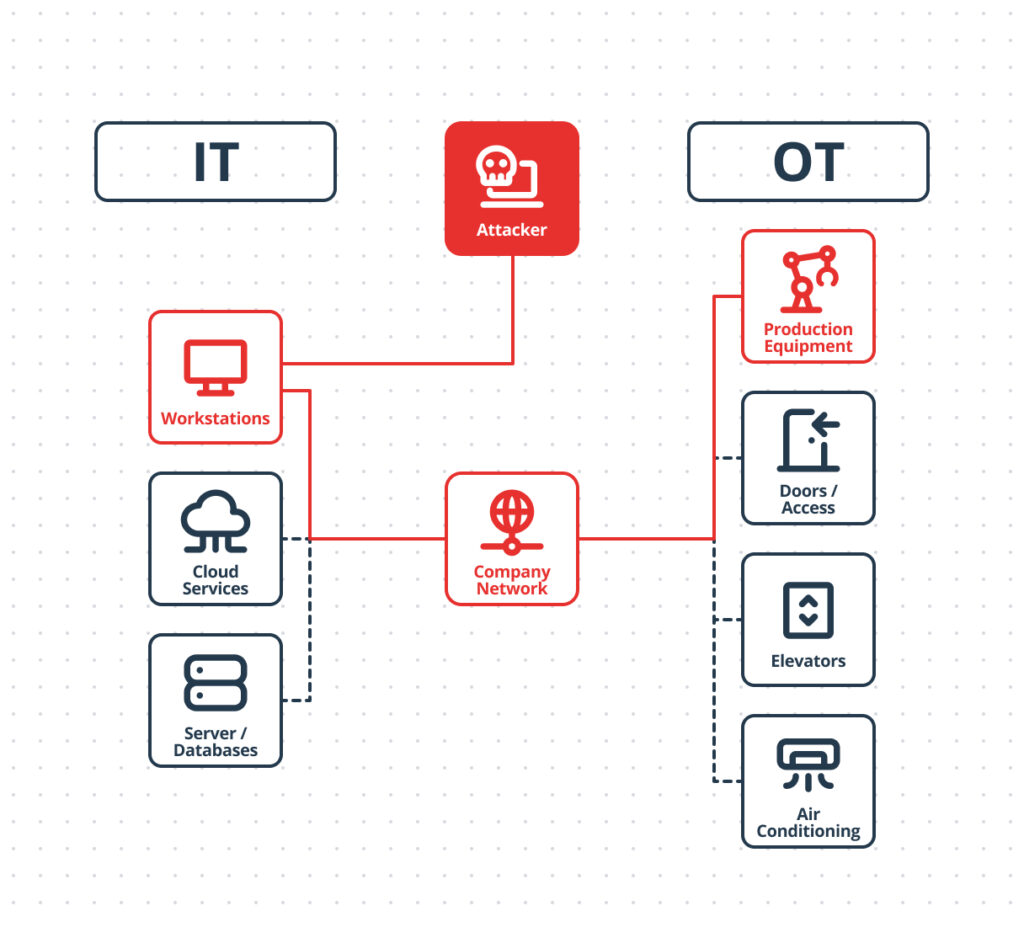
Directives like NIS2 are making OT security increasingly vital. Previously, OT systems were often isolated. Today, due to Industry 4.0, they are almost entirely networked – many having been in service for decades. Consequently, attackers often target these older systems as “gateways” into the corporate network.
To mitigate these risks, all systems on the company network must be protected. The new NIS2 Directive mandates precisely this, including protocols for responding to attacks.
Examples of OT Cyberattacks and Their Impact
What Matters Now
Effective security starts with a deep understanding of your business processes and systems. Companies must identify critical areas and design a security architecture that not only protects, but also facilitates a swift recovery.
Expertise and trained employees are indispensable for OT security. Only well-trained staff can detect and repel incidents, minimizing damage. Investing in knowledge and training is a direct investment in resilience.
All member States of the EU shall each designate a national authority responsible for cybersecurity and supervising tasks in accordance with the NIS2 directive. We supplement this with our extensive experience in OT security, particularly in integrating access control, cyber defense, and all aspects of Converged Security.

Contact us
Inform yourself in time and use expertise.
Let’s get in touch – our experts would be happy to advise you and tailor the solution you need.